To access a hidden network I2P software required - I2P router: i2pd (C++) or I2P (Java). This application contains all the internal logic of I2P and ensures interaction with other network participants. The user's operating system does not know what to do with ".i2p" domain names, so they must be passed directly to the I2P router via a proxy at a local address (127.0.0.1:4447 - SOCKS, 127.0.0.1:4444 - HTTP). The situation is similar with onion domains ".onion", which are transferred directly to the Tor router without attempting to resolve it along with other domain names (ru, com, org, etc.) through a regular DNS server.
Two titans have gained a foothold in everyday use of proxy protocols: HTTP and SOCKS. The noticeable difference between them is that an HTTP proxy cannot transmit UDP traffic, since it actually works in text mode, while SOCKS transmits information between the user and the end server in binary form, which ultimately allows you to work with any type of traffic and including UDP, which ensures comfortable use of IP telephony, and also allows you to play any online games.
HTTP headers are an integral part of the HTTP protocol, which powers almost all resources on the Internet that you access through a web browser. They transmit the user request to the server and information about the client: language, operating system version, web browser version and sometimes other identification data. Basic information about the device is transmitted in the "User-Agent" value. It is assumed that additional information about the client should help the server provide the desired page in the best possible way: in the user’s native language, adapted to his browser, and so on..
Pay attention to the User-Agent line. If we are talking about privacy, then everything is bad here. Information about the operating system and web browser, together with other transmitted values, is very unique in order to accurately track (profile) a user who may not be authorized on the site and even regularly clean cookies.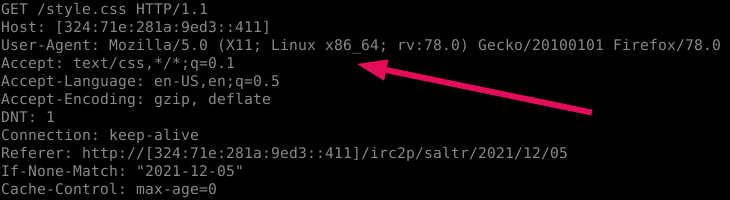
The SOCKS proxy, beloved by many, a priori does not interfere with the transmitted headers, since it transmits all information in binary form, therefore, in order to sit privately through a SOCKS proxy, you need to replace the standard headers on the side of the web browser. Otherwise, the server sees what language you prefer to communicate in, what operating system and what web browser you use. By the way, Tor only provides SOCKS proxies.
I2P routers have both types of proxies by default, but it is recommended to use the HTTP proxy, since by using it you automatically anonymize your request. The I2P router cuts off sensitive information about you and replaces Uset-Agent with the mysterious string “MYOB/6.66 (AN/ON)”, which is the same for all users. 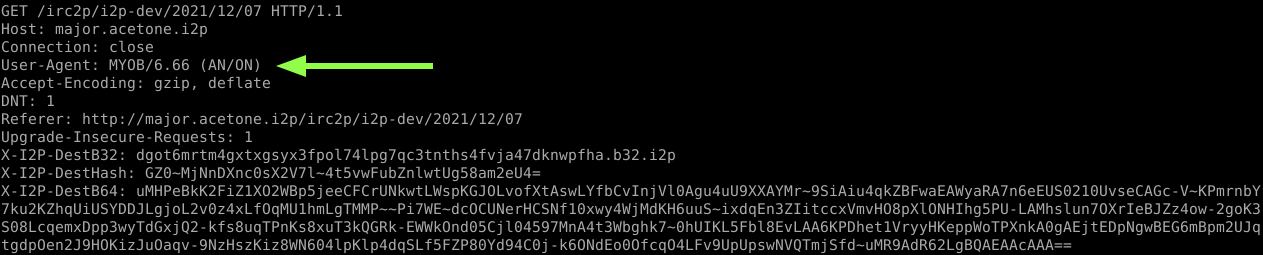
In addition, the i2pd HTTP proxy analyzes the requested URL on the fly and, if the required short domain from the “.i2p” zone is not available, offers to contact one of the on-line registrars for it. In a similar situation, the SOCKS proxy simply cannot find the destination and the user receives a standard error page in the web browser.
When asked about the meaning of the mysterious character set in the user agent of the I2P router, I answered in the development team chat:
"MYOB" can be translated as "None of your business", 6.66 is the number of the beast (a reference to the Bible, the book of Revelation aka Apocalypse), "AN/ON" is just a florid form of the word "anonymous"".
Personally, I don’t understand what the non-Orthodox number has to do with it, but I hope that this will not become a reason for banning I2P in Russia.